The growth of the security economy shows trends in security spending both by individuals, companies, and government over time. The costs of the security economy are built into almost every good we consume.
From times immemorial man has traded goods for protection, paid tolls for passage, and maintained security through a number of arrangements that could be termed a security economy. In recent years, spurred by the perception of rising crime, terrorist attacks, and the increasingly global scale of business, governments, corporations, and individuals have created a massive security economy.
The costs of the security economy include spending to prevent crime, risk management, cyber security, and a variety of other expenditures. This economy is estimated to be 20% of the US GDP (and 7% of the UK GDP). While it’s nearly impossible to track every dollar of security-related expenditures, it’s safe to say that the security economy is comprised of hundreds of thousands of businesses and providers worldwide.
The security economy is made of services that sell safety from life, property, and information-threatening events. From private contractors in America’s War on Terror to internet security analysts to traditional security firms focusing on alarms, fires, locks, and safes, the range of actors in the security economy hold one thing in common: they are services that sell safety from life, property, and information threatening events.
Terrorism
Perhaps the largest driver in the growth of the security economy is the United States’ War on Terror. Since 9/11, security spending to combat terrorism has ballooned to a behemoth scale. A Washington Post report from 2010 notes that there are an astounding 1,271 government organizations, and 1,931 private companies working on programs related to counter-terrorism, homeland security, and intelligence. Of those workers, 854,000 hold top-secret clearances.
Department of Homeland Security
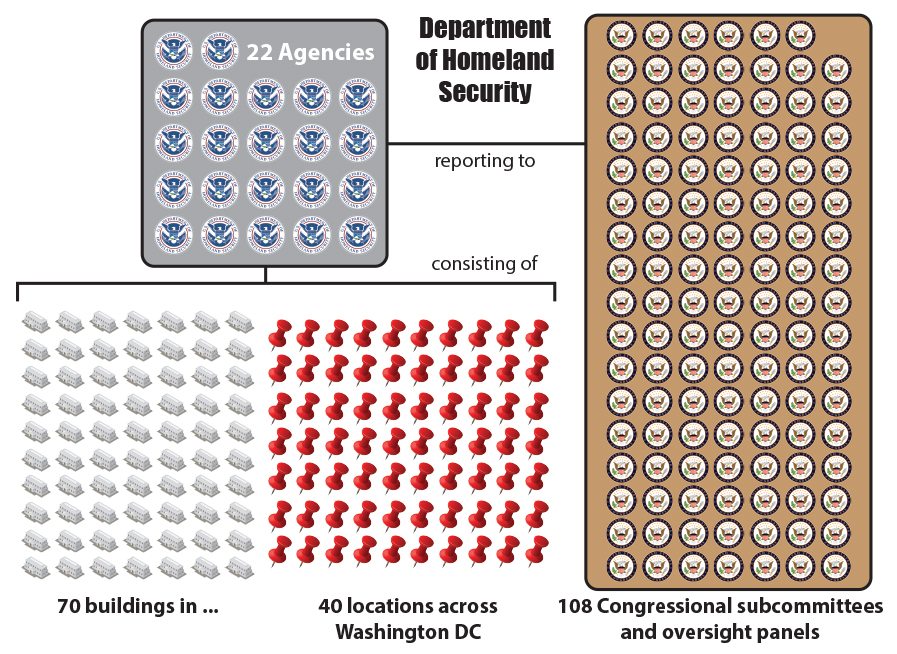
Though the War on Terror has resulted in the capture or killing of many high-profile terrorist suspects, the efficiency of spending on such a scale is doubtful. Roughly 3,000 Americans have lost their lives to terrorist attacks in the past decade. For each American victim of a deadly terrorist attack, the US spends roughly $500 million. With two wars costing upwards of $6 trillion, and a proposed $56 billion increase in defense spending for 2015, the cost per life’s protected starts to look suspect. Regardless, it’s all the better for the growing security economy.
The scale of private contractor use in the War on Terror is unprecedented and has led to the creation of many boutique defense contractor firms who hire out everything from support units to ex-special forces troops. With the withdrawal from Afghanistan beginning in 2013, over 110,000 private contractors remained in defense roles. At that point outnumbered U.S. troops by 40,000. With the current insurgency claiming large portions of Iraq, there are only a few hundred U.S. troops still on the ground. Yet over 5,000 defense contractors are on hire by the Iraqi government.
Cyber Warfare
Similar to terrorism, cyber warfare shows the major distinction between 21st-century security threats and the threats of previous centuries. Advanced technology allows small technically proficient groups the ability to undermine the security of larger organizations. Much like guerrilla tactics in former military conflicts, large established forces of systems-security analysts can’t know who they are being attacked by, and from where they are being attacked. There’s a jungle of technology out there, and those who know how to exploit it best are often mercenaries.
To be clear, cyber warfare involves state-sponsored hackers who attack the computers or networks of sensitive resources within another nation. Sensitive resources can include military, defense, and weapon manufacturers, and power grids. Perhaps the scariest economic sectors to target could be shutting down stock markets, or major e-commerce sites.
As it’s often unclear who exactly is responsible for attacks, the “state-sponsored” criteria for cyber warfare are often hard to pin down. For this reason, Eugene Kaspersky, founder of Kaspersky Lab, for which the anti-virus software is named, concludes that “cyberterrorism” is a more accurate term. Regardless of what you call it, the 21st century has seen a massive influx of both cyber attacks and increasing cyber-defense infrastructure.
Cyberattacks By Country
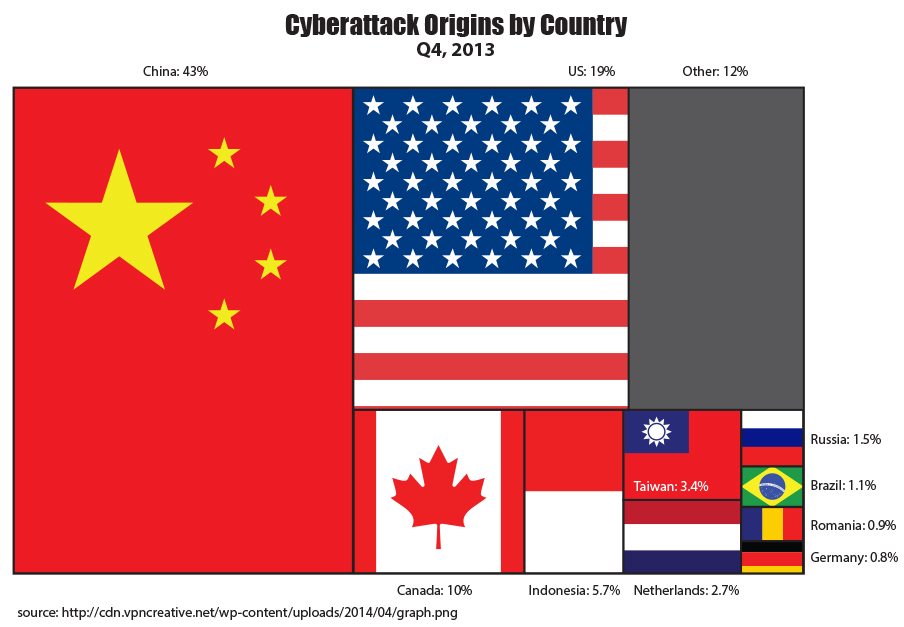
As seen in the graphic above, there are but a few large-scale players in the cyber war game. Starting in 2014, 43% of attack traffic online began in China, with only 19% originating in the US. The above information is based on the location of IP addresses from which attack traffic originated, a measure that can be tricked by hackers, but it still provides a glimpse into who the largest players are. To see a live look at DDoS attacks worldwide, check out the linked graphic.
Chinese hacker groups are particularly notorious for targeting businesses and government organizations in the US. “Hidden Lynx,” the name of one of the most sophisticated Chinese hacker groups, was caught attempting to hack the Gmail accounts of human rights activists in 2013. While the Chinese government denies control of the hacker group, it is known that several high-profile Chinese hackers are members of the Chinese military.
While Chinese cyberattacks are potentially the most interesting when talking about US cyber defense, the US is responsible for what is potentially the most effective and destructive public cyberattack to date. Operation “Olympic Games” involved the introduction of “worms” into the computers controlling an Iranian Uranium Refining Plant. The worm programs varied so as to make them hard to detect, and were introduced on numerous occasions over several years.
Through slowing down and speeding up the plant’s centrifuges many became unbalanced, and some even exploded. By destroying centrifuges at strategic moments, the US was able to massively slow down the uranium refinement process. Common mechanical failures in the centrifuges were mimicked, allowing the operation to continue undetected for some time. Operation “Olympic Games” is an example of how much “concrete” damage can be produced with simply a few maliciously programmed computers.
Risk Management
Risk management can come in a variety of guises, from kidnapping insurance to armed guards, to corporate strategy, and fire alarms. IT risk management, however, is one of the fastest-growing risk management sectors. While anyone with sensitive data is at risk, the rise in cyber warfare and hacking is particularly worrying to banks. A report by IDC Financial Insights notes that DDoS cyber attacks were 47% more frequent in Q1 of 2014 than a year prior.
In an effort to respond and protect our most sensitive data (financial data), the same report estimates a total of 17.1% of overall IT spending by banks will be spent on IT risk management. For every 4 dollars spent on internal IT infrastructure, apps, mobile banking, email platforms, and a million other IT matters, 1 dollar will be spent on risk management.
Over the last decade and a half, the emergence of a global economy has also pushed risk management–in a more general sense–to the forefront of business decision-making. 9/11 reinforced fear of terror and the need to ensure personal safety into the spotlight of western media and thought. The recession that followed throughout much of Europe and the US showed that even our hallmark industries can misjudge the need for structural changes, and fall into bankruptcy.
Meanwhile, an increasingly global economy raised the bar of competition higher than ever. In previous years, the quality of a product set it apart from its competition. Today, businesses from around the globe provide equally high-quality products. What sets them apart is their ability to mitigate risk (local, and global), and ride out tough times.
Changes in Risk Management
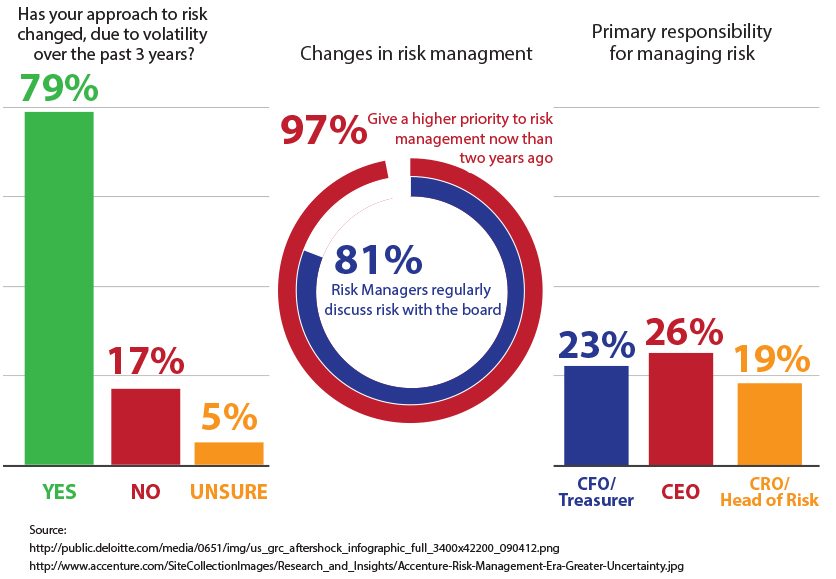
The International Organization of Standardization (ISO) provides one of the most widely used risk management terminologies. While criminal harm as outlined in previous sections on other aspects of the security economy can be processed by risk management principles and methods, risk management also tackles many of the structural problems that led to the downfall of companies such as Merrill Lynch, AIG, Washington Mutual, Lehman Brothers, and Arthur Andersen during the recession.
The insane race for growth that led to the subprime mortgage crisis is answered by two of ISO’s top risk management principles: (1) create new value (even at the expense of short term growth), and (2) be dynamic, iterative, and responsive to change. The ISO method for risk management includes the following steps.
- Identify, and characterize threats.
- Assess the vulnerability of critical assets to specific threats.
- Determine the risk (i.e the expected likelihood and consequences of specific types of attacks on specific assets).
- Identify ways to reduce those risks.
- Prioritize risk reduction measures based on a strategy
While that may seem somewhat abstract, the rise in risk management in business thought goes hand in hand with the massive movement in security spending. After all, what else is the protection of a business’s future than the safety of property, information, and even life from threatening events?
Related:
- How Can I Get Into Cybersecurity?
- 25 Online Cybersecurity MBA Programs
- Top 10 Online Cyber Security Associate
- 10 Online Cyber Security Undergraduate Certificates
- Top 10 Online Cyber Security Degree Programs